At the University Library System (ULS), we collect, use and store selected information about our patrons required to support our mission and services. We take the responsibility of ensuring safe and transparent management of this data seriously.
Privacy is a core value of libraries. In the ULS, we adhere to the privacy principles established and shared by the library profession. The American Library Association (ALA) maintains several privacy-related statements and policies that inform our practice1, including the foundational statement in its Library Bill of Rights, "All people, regardless of origin, age, background, or views, possess a right to privacy and confidentiality in their library use.2 "
Moreover, concerning the management and security of sensitive data, our practices are subject to regular audits by the University's Internal Audit Department. We do not share personal information with third parties beyond those we have contracted to provide library services. These parties are subject to a security review conducted by Pitt Information Technology.
The information below will provide more detail about the information we collect and maintain and examples of how we use this information to improve our services.
Every member of the University community has a library account that allows them to access library materials, request an interlibrary loan, or pay library fines. Your information to create this account is sourced directly from the University of Pittsburgh's institutional records and is stored securely within ExLibris's North American data centers. The University records regarding your identity are supplemented with your library transaction records. You can access your account to review your information by logging in to PittCat.
After you return materials borrowed from the Library's physical collections, we remove all links between your account and the items you had checked out.
Access to our digital resources is often provided via websites and licensed databases that we do not maintain. We do make every effort to protect your privacy when negotiating licenses. Please note that ULS is not responsible for the privacy practices or the content of these third-party tools; therefore, we encourage you to read the policies associated with these third-party tools before using them. For instance, some websites or databases may require additional registration with the vendor, who may ask for personal information. In our licensing, we endeavor to restrict vendors from using this data for purposes other than those for which it was collected. Also, when you access third-party subscription databases outside Pitt's IP range (e.g., from home), the authentication services (such as EZProxy or Shibboleth) may collect your username and IP address for monitoring for any unauthorized access.
When you log into library computers and group study room monitors, we collect information about when you logged in and how long you stayed connected. These logs are deleted after one year. We do not track any websites you accessed, and the software used on these machines is never linked to individual users. However, since our computers run on the Microsoft Windows operating system, the vendor may collect some usage information. Still, it never includes any personally identifiable information (like names, usernames, or passwords).
When you connect to wireless networks in our buildings, your username, time, and duration of access will be captured and logged with Pitt IT.
When you use ULS websites, our web servers collect technical information from your web browser. Our web server may use browser cookies or other technologies to maintain session and preference information. In addition, we track traffic to our websites with Google Analytics, which uses cookies.
We also collect information that you may enter into our web-based forms. For instance, when you initiate a reference chat session, book a library study room, register for our workshop, or respond to our survey. If you submit personal information via one of these platforms, we use your personal information only for the purpose for which you submitted it.
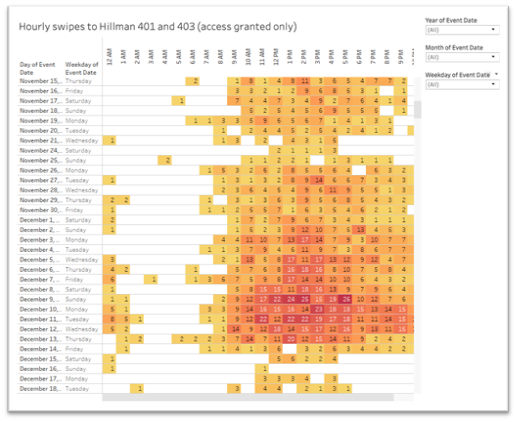
Some spaces in our buildings are controlled by swipe card access. Pitt's Integrated Security Services is responsible for the management of the data collected using the swipe cards. Some of this information, de-identified and in aggregate, may be shared with us to understand the use of these spaces better.
How we use this data: examples
Data captured when you use our services, as listed above, may be used by us to understand trends in the utilization of our resources and to make data-informed decisions about our services. Please note that we do not store any personally identifiable information for such analyses. Analyses are always performed, and data is reported in aggregate.
Below you can see examples of reports we compile from usage data we capture.
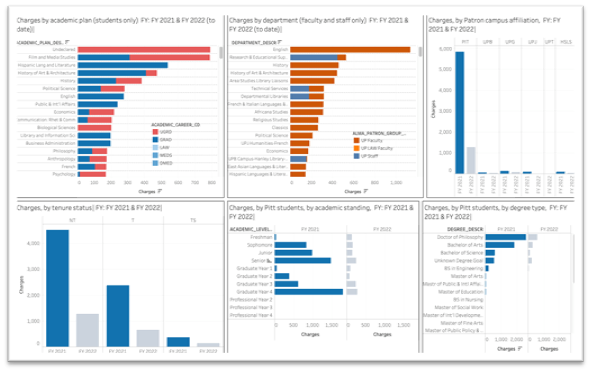
- Use of physical materials: We analyze data from our library management system to understand user engagement with our physical collections. We look at these at the level of individual departments and type of patron to help us plan our new acquisitions and review our collections development policy and practices.
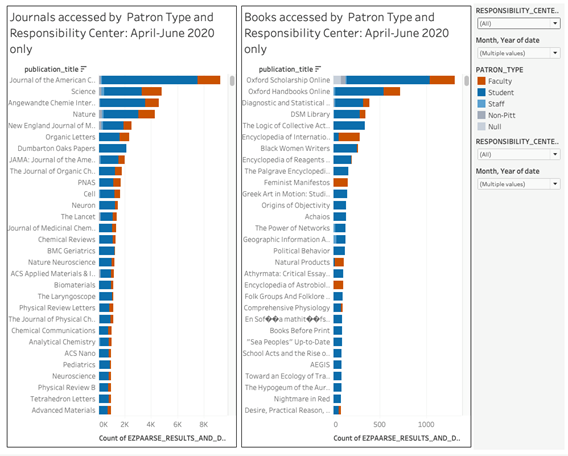
- Use of digital materials: We collect logs that show our patrons' access to electronic journals, books, and databases we subscribe to. The logs are anonymized and only contain readers' departmental affiliation and status (faculty/student/staff). This information clarifies usage patterns of electronic resources, allows us to understand the value of various e-resources to our users, and supports us in vendor negotiations.
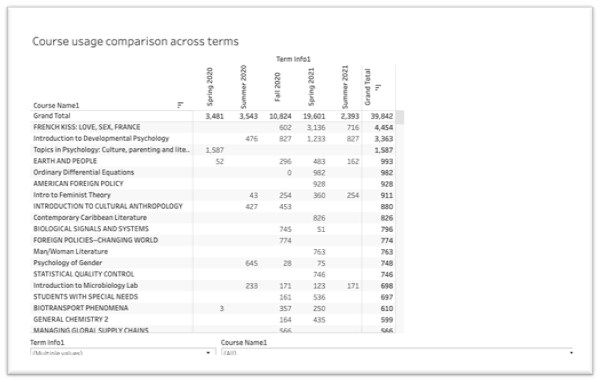
- Usage of course reserve materials: course reserves are materials that instructors ask us to make available for their students for the duration of their courses. Understanding the volume and usage of these materials allows us to plan for the resources needed to make them available.
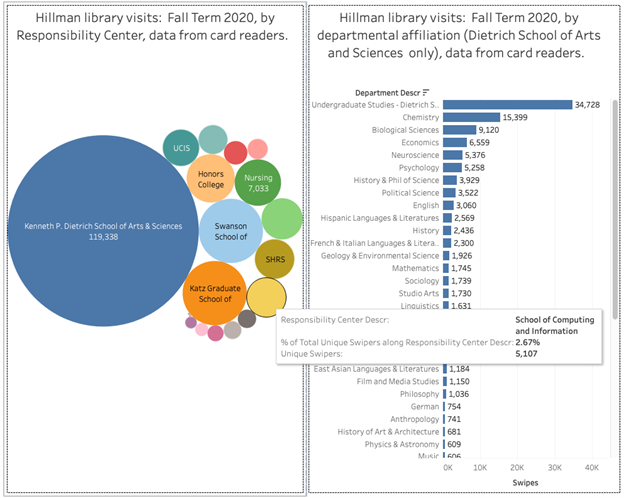
- Space utilization: Swipe card data allows us to understand the use of our spaces by different user groups and the patterns of that use throughout an academic year, days, and times of the day. This information allows us to, for instance, plan our opening hours and staffing levels.




